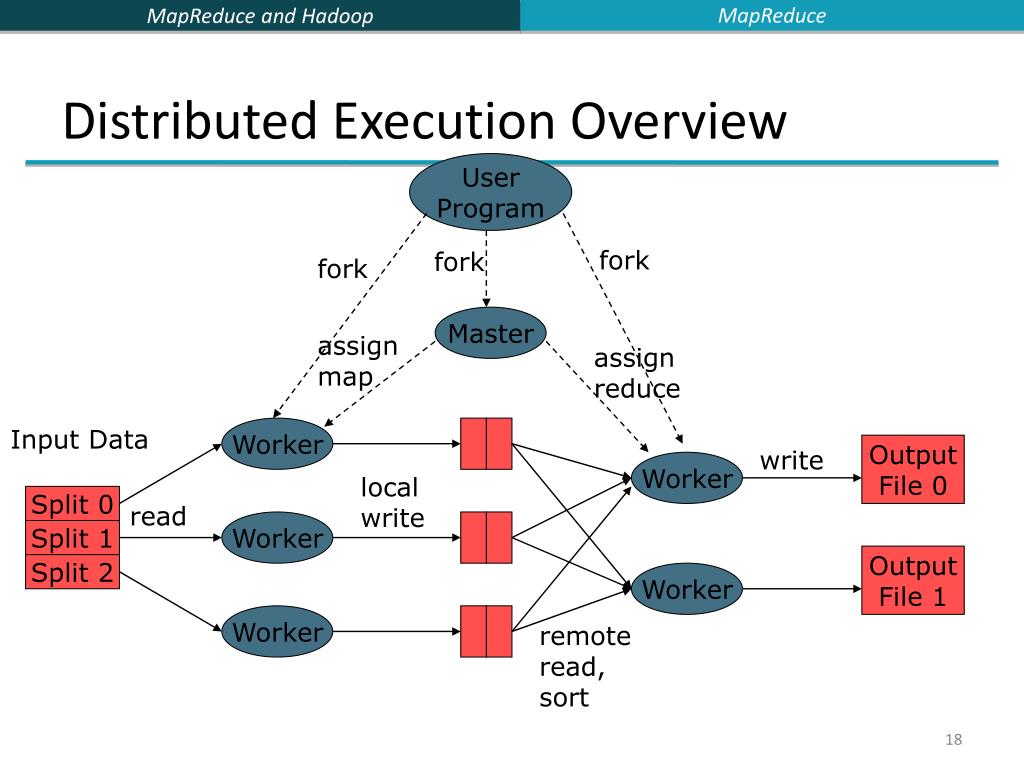
Map Execution Paths Through Application. Without a thorough understanding of the layout of the application, it is unlkely that it will be tested thoroughly. Not just because the tester has no view of the code paths through the application, but even if they did, to test all code paths would be very time consuming. Before commencing security testing, understanding the structure of the application is paramount. Map the target application and understand the principal workflows. Created by the collaborative efforts of cybersecurity professionals and dedicated volunteers. How to Test In black-box testing it is extremely difficult to test the entire codebase.
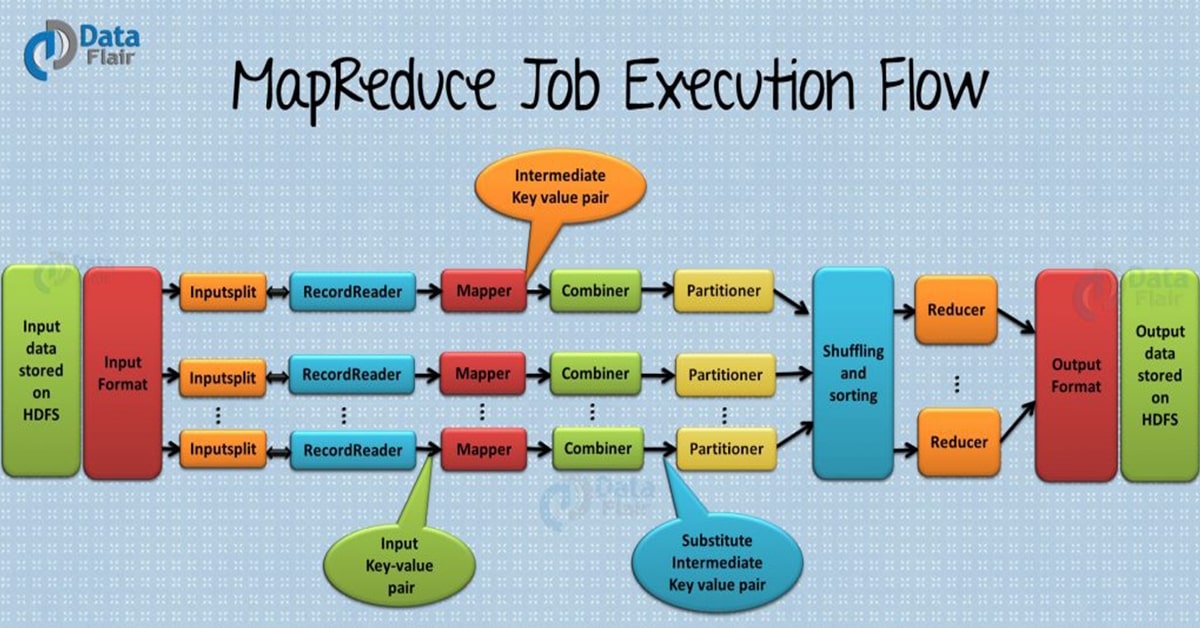
![MapReduce job execution flow [20] | Download Scientific Diagram](https://www.researchgate.net/profile/Neda_Maleki2/publication/333667435/figure/download/fig2/AS:767941607952385@1560102955617/MapReduce-job-execution-flow-20.png)
Map Execution Paths Through Application. The OWASP ® Foundation works to improve the security of software through its community-led open source software projects, hundreds of chapters worldwide, tens of thousands of members, and by hosting local and global conferences. Test Objectives Map the target application and understand the principal workflows. Not just because the tester has no view of the code paths through the application, but even if they did, to test all code paths would be very time consuming. Focuses on mapping the flow, transformation and use of data throughout an application.</li>\n<li>Race – tests multiple concurrent instances of the application manipulating the same data.</li>\n</ul>\n<p dir=\"auto\">The trade off as to what method is used and to what degree each method is used should be negotiated with the appli. How to Test In black-box testing it is extremely difficult to test the entire codebase. The Web Security Testing Guide (WSTG) Project produces the premier cybersecurity testing resource for web application developers and security professionals. Map Execution Paths Through Application.
The OWASP ® Foundation works to improve the security of software through its community-led open source software projects, hundreds of chapters worldwide, tens of thousands of members, and by hosting local and global conferences.
Map the target application and understand the principal workflows.
Map Execution Paths Through Application. Map Execution Paths Through Application Summary Before commencing security testing, understanding the structure of the application is paramount. The railroad lines and ownership throughout the state. To zoom in on the Iowa state road map, click or touch the plus (+) button; to zoom out, click or touch the minus (-) button. Before commencing security testing, understanding the structure of the application is paramount. Iowa is a state in the Midwest. Select a section of the state map.
Map Execution Paths Through Application.